This is an obvious guide on how to avoid malware. The reason I call it “obvious” is because the tips you see in here are very easy, low level, and you’ve probably heard of them before. When we talk about malware we are referring to a generic description of any unwanted items on your computer. For example these are things such as Viruses, Trojan, Ransomware, Adware, Spyware, Rootkits, and anything you don’t want on your computer. While this guide is for those here at work in CAES, these are tips you can use at home as well.
Browsing Habits
One question I always get when clearing malware off someone’s computer is, ”How did I get this?” Well most of the time, the answer isn’t obvious. However the likelihood that the user picked up the malware while browsing the internet is very high. Here are some tips on how to avoid malware while browsing the internet.
Don’t Wander Off
Think about the internet as an Iceberg, we only see a very small portion of it and the rest is underwater. What we can see above water are the sites we most commonly visit. These are your Facebook, MSN, Amazon, and Google kind of websites. These websites are generally safe and don’t pose a threat to your computer. The iceberg below the surface are the sites out there most people don’t commonly visit and could potentially be harmful to your computer. In this blog we will refer to them as sub-surface sites. Not every sub-surface site is malicious, but they usually don’t have the enterprise level of security, resources, or public reputation of the sites above the surface. How do you end up wandering below the surface?
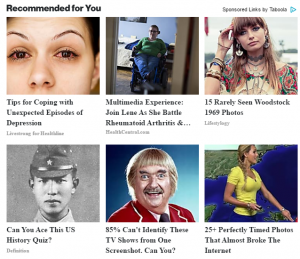
Facebook links/Clickbait– Be weary of what your friends are linking. Just because they went to that site, doesn’t always mean it’s safe.There are many malicious sites designed to be shared on Facebook and bring victims to their site. Facebook has been cracking down on this and while the results are positive, you should still be cautious of what you click.
Free Movie/TV Streaming– There are many websites out there with the promise of all you can watch tv and movie streaming for free. These website grow every day and pull millions of visitors. This is the top poor browsing habit I see in relation to malware. These websites, even if not malicious themselves almost always feature links to sites with malware or malicious ads.
Foreign Websites– Now this one is a very broad reaching group and as a multi-national university and college we often have many users visiting foreign sites. Being in the position we are in, this browsing habit may be hard to avoid. Foreign websites don’t all have to adhere by the same standards/laws that websites here have to. While the US still hosts a large percentage of the malicious websites in the world, users should still have caution when visiting foreign sites. Sites from countries such as Russia, China, South Korea, and Peru should be visited with caution.
Adult Websites– This is one everyone should know and should go without saying. It should also go without saying that this should not be a problem for any computers in the workplace since you should NOT be visiting these sites at work or on CAES computers. Adult websites have always been closely linked to malware. Stay away!
If you are ever worried about the safety of a website you can always research the site before going to it. Tools such as Google Transparency Report let you look up info about the website and give you a safe or not safe status of the webpage. Most browsers do contain protection built in and will prompt you before accessing a harmful site, but this does not always save you.
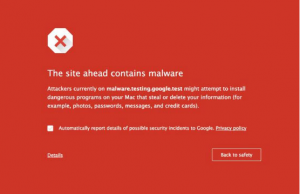 This is what you see when Chrome blocks a known malicious webpage.
This is what you see when Chrome blocks a known malicious webpage.
Malicious Ads
Malicious ads are advertisements that either link to harmful websites or contain malware within them. With the latter of those, you don’t even have to click on the ad for your computer to get an infection. These advertisements could be on any site you visit. Popular websites such as New York Times have even used malicious advertisements without knowing beforehand. Websites who have the resources, do keep tabs on the ads running on their pages and ensure that the ads on their sites are safe. The sub-surface sites don’t usually have those resources and that lack of screening can bring in ads that are harmful. My recommendation is to use an ad blocking add-on for your browser. While ad blocking has its own ethical argument attached, from a security perspective it is very beneficial. Ad blocking can block out harmful ads if you do find yourself in potentially harmful websites. However, ad blocking does not mean you’re completely safe and you should still use caution when browsing sub-surface sites.
These are typical clickbait ads that can be found on many sites. While these particular ads may not be malicious, they can eventually lead to malicious websites.
Manage your Downloads
Another common gateway for malware into your computer is through what you download and/or install. When you download anything to your computer you could be allowing in malware and you must be conscious of what it is you are allowing in, especially if you are installing a software.
Next Next Next…
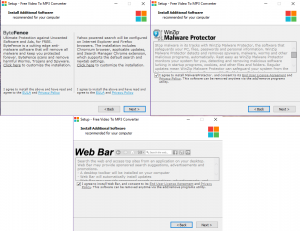
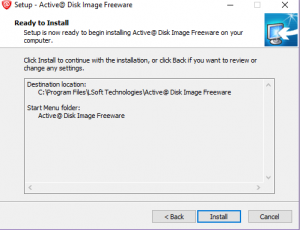
We have all installed a software with an annoying amount of prompts in the installer window. A lot of us find ourselves clicking “Next” as fast as we can so that the software will install. What we miss sometimes is that the installer asks us if we also want to install some other software in addition. These are things such as toolbars or optimization software. A lot the time, we don’t see that this is being added to our install because we are clicking through the prompts to quickly or the installer has hidden the options for the additional software. The additional software is commonly malicious and can serve as a gateway for more malware to come in to your computer. Always read the prompts on your installers and see what they are asking. Many installers include a summary of what is going to be installed before it starts actually installing. If you see something you don’t recognize, go back and read the pages of the installer.
This is an example of a software install adding additional and potentially harmful software.
Many installers feature a page that show you everything that will be installed, this is what it looks like.
First Party
When you are installing software, always make sure to get it from the company that makes it. For example, let’s use Silverlight. Silverlight is a Microsoft software that is used by many other applications. If you were to download Silverlight, you may find yourself putting in “Silverlight download” into a search engine. This is a completely fine way of finding the download source. However, depending in the search engine, the results you see up top may or may not be the first party site for that software. Below is a comparison between Google and Yahoo searches for the same thing. Notice on the Yahoo search, the first result is a third party site. For downloads of any software you want to avoid these kinds of sites and always use the first party site. If you are unsure of who makes the software, a simple search should always return the answer.
The green marks represent results from the first party website and reds mark third party sites. Not all reds are malicious, but there is no reason to risk using them when you can always download from a first party.
You must install this to continue
There are many malicious websites out there that will load and then require that you install a software to make the website work. Maybe is a video software that will allow you to view the video on the site or a font that the site uses. If the site requires that you install a software to view it, leave. Simple. If it auto downloads and installer for you, delete it and do NOT run it.
Email attachments/links
Email attacks are well known, but here are some tips on how to avoid malicious emails. If someone you don’t know sends an email with an attachment or a link, don’t open it. Most of these are pretty obvious and are easy to avoid, but others can be well constructed and hard to catch. Many of you work in positions that require you to open attachments from users outside our organization everyday. Both Outlook and Web App for our email have an option to preview the document in the email without opening Word or Acrobat. This is a safe way to look at any document you receive. If you do download the attachment and open it up you could be allowing malware onto your computer. Please do be cautious of clicking links sent in emails, clicking and opening the wrong link can have big ramifications even if you don’t download anything or the webpage doesn’t open to anything. If an email seems even the least bit fishy or just off, high chance it’s malicious.
In any case you suspect an email has malcontent please forward it to us at OIThelp@uga.edu.
File Sharing
Whether you are using a P2P client like UTorrent or a direct download site like Megaupload, you could easily be allowing malware into your system. I am going to approach this the same way I approached Adult Websites in the last section. If you don’t want to malware, don’t participate in file sharing. Also DON’T do this at work! Simple!
Active Protection
In addition to having good browsing habits and managing your downloads, having an active anti-malware subscription can also help you avoid malware infections. Active Protection is the constant, always on monitoring of your computer by an anti-malware software. Not all anti-malware software has active protection. If you have downloaded a free version of an anti-malware software, it is likely that it is only a scanner. A scanner can only scan your computer for infections when it is prompted, it does not prevent infections but only removes them.
No Perfect Solution
I often hear, “Well I have protection, how did I get an infection?”. The truth is, there is no perfect anti-malware software. Some are better than others, but none will prevent everything.
Whats available to me?
Here in CAES you have three active protection softwares available to you. The first is the built in protection for Windows, Windows Defender. Defender is far from perfect and I don’t recommend using Defender for your protection software alone. The next is the University’s protection software, Trend Micro. At the college level we have a subscription to MalwareBytes Anti-Malware. If you are in need of any of these installed, please let us know!
At Home?
While Trend Micro and MalwareBytes can only be used on computers owned by CAES, there are some options for home. A good, free active protection software is hard to come by. I recommend Bitdefender for those looking for a free active protection software for their personal devices. Anti-malware software is much like anything else, you get what you pay for. If you decide to go free, your options in software and what that software can do is very limited. If you are looking a good active protection subscription for your personal devices, I recommend a MalwareBytes subscription.
But I am on a Mac!
For your CAES devices we have MalwareBytes and Trend Micro installers for those! For personal devices we recommend Sophos and Avira.
Software to Avoid
Anti-malware software to avoid are the ones that involve themselves in with every part of the computer to monitor for threats. These softwares are very controlling and manage your settings for your operating system and your web browsers. While this is done to increase your security, it can also cause problems with websites and can become a nuisance when you are just trying to use your computer normally. A mark of good anti-malware software is that it runs almost entirely in the background and does not interfere with your general use of the computer all while keeping you safe. Softwares to avoid are Norton, McAfee, and AVG.
I’ve Got Malware! What now?
If it is a CAES machine, please contact the Service Desk immediately! You can reach us at 706-542-2139 and OITHelp@uga.edu. If it is your personal device, stay tuned for a malware removal guide in a later blog!